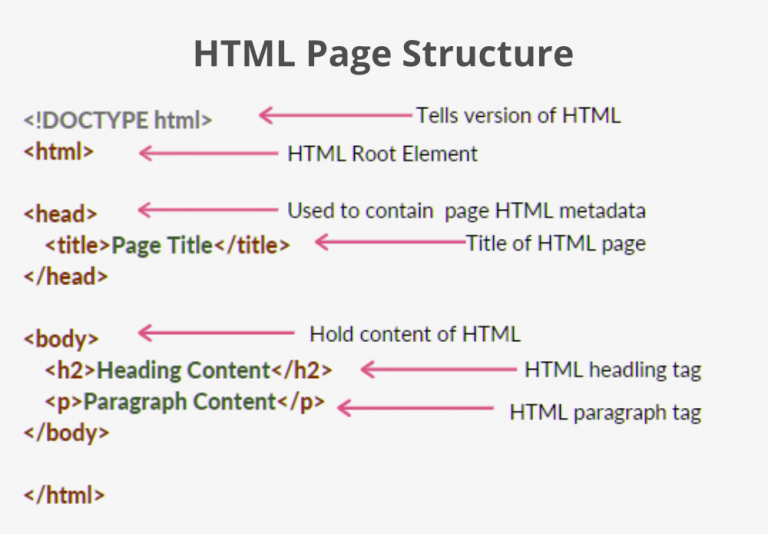
किसी डोमेन को सर्वर या होस्टिंग से कैसे कनेक्ट करें
डोमेन नाम सेट करना आपके विचार से कहीं ज़्यादा आसान हो सकता है। एक बार आपका डोमेन नाम पंजीकृत हो जाने के बाद, आपको इसे अपने होस्टिंग सर्वर से कनेक्ट करना होगा।1. आपके पास Namecheap के साथ एक होस्टिंग प्लान है।
2. आपके पास कहीं और एक होस्टिंग प्लान है और आपको अपने डोमेन के लिए नेमसर्वर दिए गए हैं।
3. आपके पास अपना सर्वर है या आपको डोमेन को अपनी होस्टिंग से जोड़ने के लिए होस्ट रिकॉर्ड का एक सेट दिया गया है।
1. आपके पास Namecheap के साथ एक होस्टिंग योजना है।
अगर आपके पास हमारे साथ स्टेलर, स्टेलर प्लस या स्टेलर बिज़नेस प्लान (या पुराना वैल्यू, प्रोफेशनल, अल्टीमेट, बिज़नेस प्लान) है, तो आपको डोमेन को हमारे वेब होस्टिंग DNS नेमसर्वर (dns1.namecheaphosting.com और dns2.namecheaphosting.com) पर पॉइंट करना होगा। अगर डोमेन Namecheap के साथ पंजीकृत है, तो यह आपके Namecheap खाते में निम्न तरीके से आसानी से किया जा सकता है:
1) अपने Namecheap खाते में साइन इन करें (साइन इन विकल्प पेज के हेडर में उपलब्ध है): 2) बाएँ साइडबार से डोमेन सूची
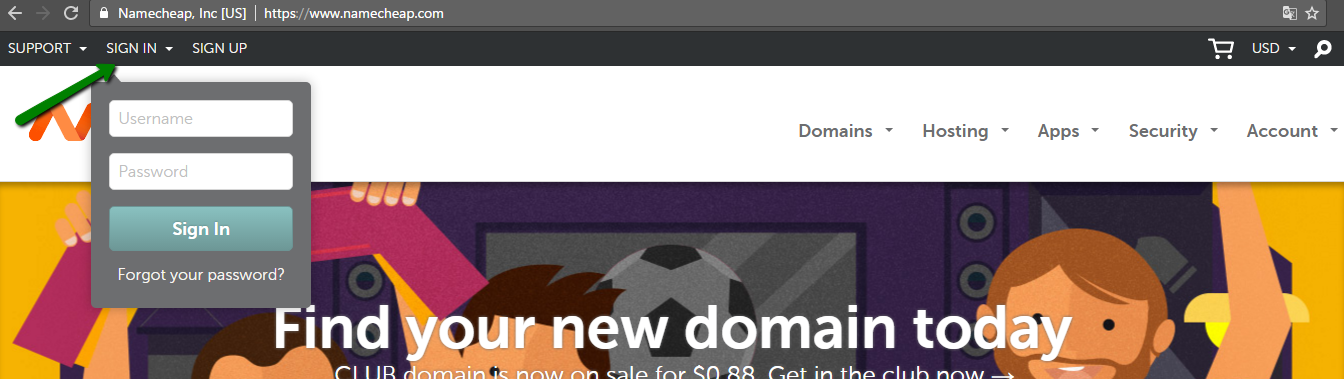
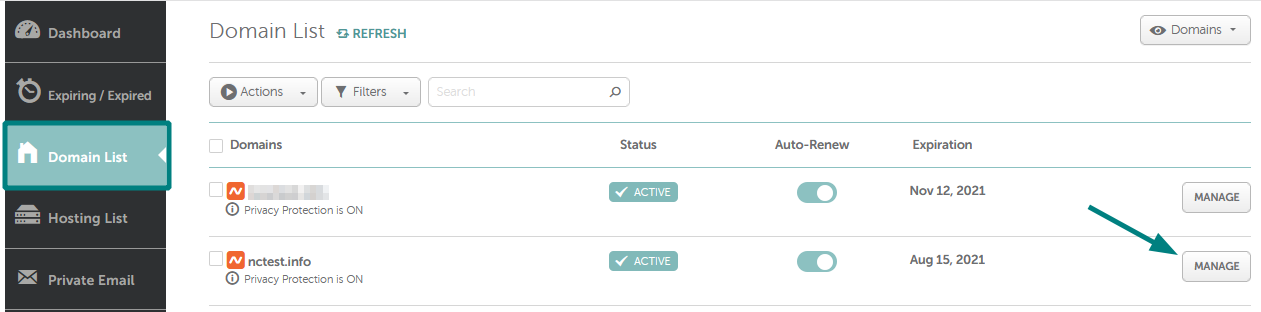
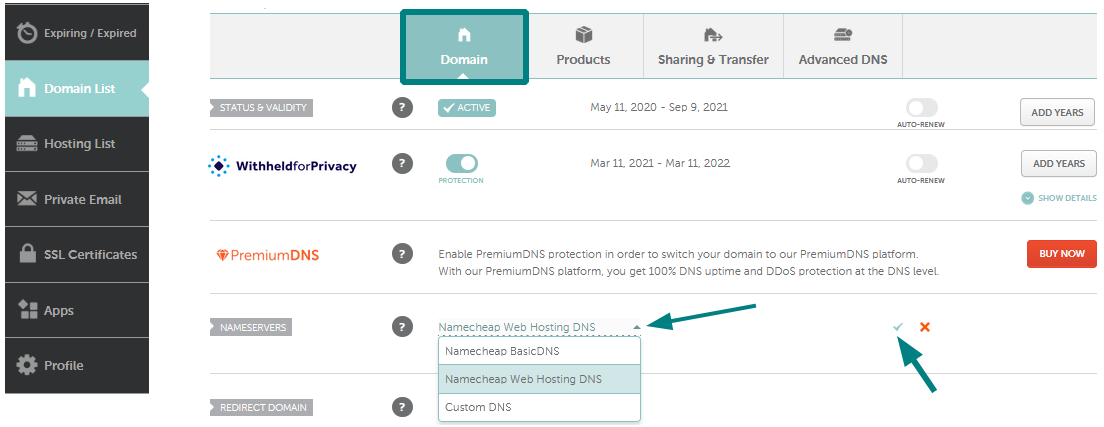
चुनें और सूची में अपने डोमेन के आगे स्थित मैनेज बटन पर क्लिक करें: 3) नेमसर्वर सेक्शन ढूँढ़ें और ड्रॉप-डाउन मेनू से Namecheap वेब होस्टिंग DNS चुनें। उसके बाद, परिवर्तनों को सहेजने के लिए चेकमार्क आइकन का उपयोग करें:
अगर आपका डोमेन GoDaddy के पास पंजीकृत है, तो यहाँ दिए गए चरणों का पालन करें ।
2. आपके पास कहीं और होस्टिंग योजना है और आपको अपने डोमेन के लिए नेमसर्वर प्रदान किए गए हैं।
अपने होस्टिंग प्रदाता से प्राप्त नेमसर्वर के माध्यम से किसी डोमेन को किसी तृतीय-पक्ष सर्वर या होस्टिंग योजना से कनेक्ट करने के लिए, आपको इन नेमसर्वर को अपने डोमेन के लिए कस्टम के रूप में सेट करना होगा। आप इसे निम्न तरीके से कर सकते हैं:
1) अपने खाते में साइन इन करने के बाद, बाएं साइडबार से डोमेन सूची का चयन करें और सूची में अपने डोमेन के बगल में प्रबंधित करें बटन पर क्लिक करें। फिर नेमसर्वर अनुभाग ढूंढें और ड्रॉप-डाउन मेनू से कस्टम DNS
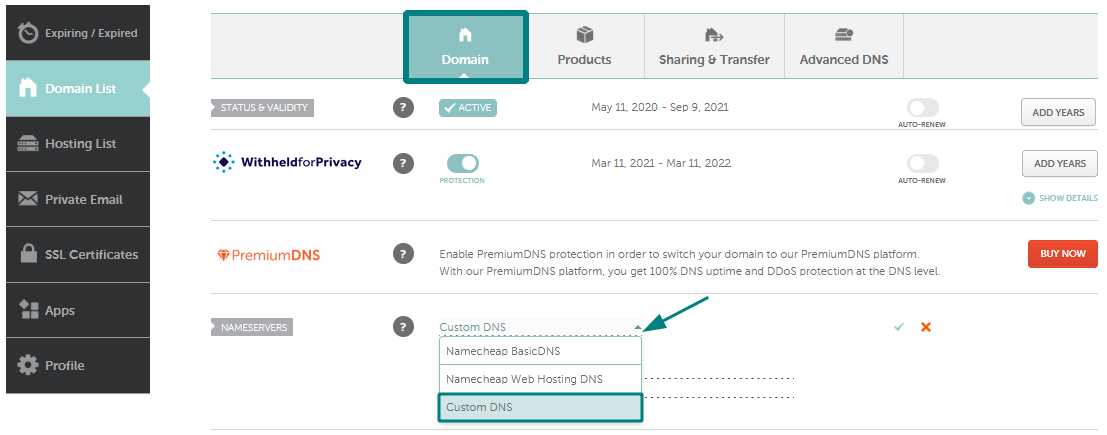
का चयन करें: 2) उसके बाद, प्रत्येक पंक्ति में एक-एक करके अपने होस्टिंग नेमसर्वर दर्ज करें (यदि आपको 2 से अधिक नेमसर्वर सेट करने की आवश्यकता है, तो नेमसर्वर जोड़ें लाल बटन दबाएं)। जब नेमसर्वर दर्ज किए जाते हैं, तो परिवर्तनों को सहेजने के लिए हरे रंग के चेकमार्क को दबाएं : नेमसर्वर अपडेट

के बाद आपके डोमेन को दुनिया भर में ठीक से हल करने में लगभग 24-48 घंटे लग सकते हैं
3. आपके पास अपना स्वयं का सर्वर है या आपको डोमेन को अपनी होस्टिंग से जोड़ने के लिए होस्ट रिकॉर्ड का एक सेट प्रदान किया गया है।
जब आपके पास अपना होस्टिंग सर्वर हो और आपको उसका आईपी पता पता हो, तो आप अपने डोमेन को सर्वर से कनेक्ट करने के लिए A रिकॉर्ड्स सेट अप कर सकते हैं। इसके अतिरिक्त, कुछ होस्टिंग प्रदाता आपको वह आईपी एड्रेस दे सकते हैं जिसका इस्तेमाल आपके डोमेन को आपकी होस्टिंग योजना से कनेक्ट करने के लिए किया जाना चाहिए। ऐसी स्थिति में भी A रिकॉर्ड्स बनाए जाने चाहिए।
ध्यान दें कि यह तभी किया जा सकता है जब डोमेन हमारे BasicDNS/ PremiumDNS /FreeDNS नेमसर्वर का उपयोग कर रहा हो। आप A रिकॉर्ड्स निम्न तरीके से सेट अप कर सकते हैं:
1) अपने खाते में साइन इन करने के बाद, बाएँ साइडबार से डोमेन सूची चुनें और सूची में अपने डोमेन के आगे स्थित प्रबंधित करें बटन पर क्लिक करें। फिर पृष्ठ के शीर्ष पर उन्नत DNS टैब पर जाएं : 2) होस्ट रिकॉर्ड अनुभाग
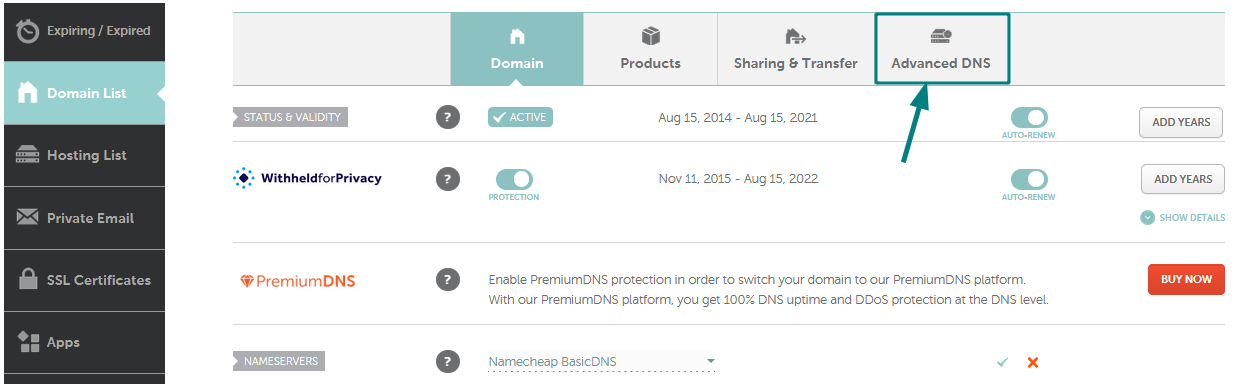
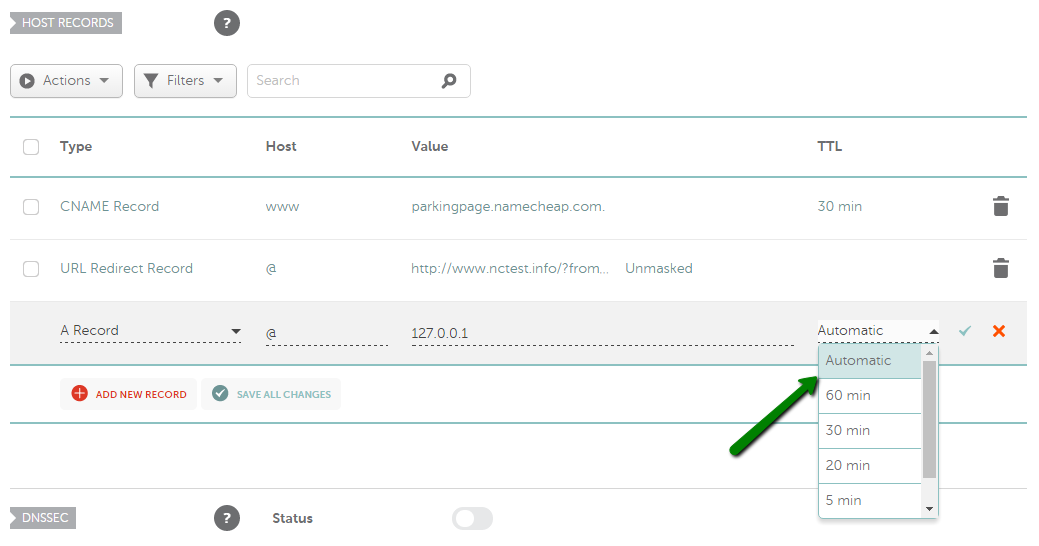
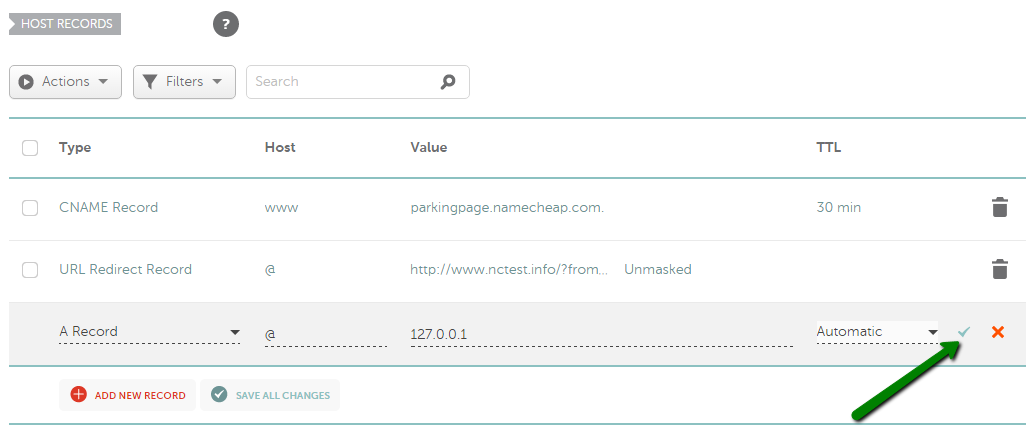
ढूंढें और नया रिकॉर्ड जोड़ें बटन पर क्लिक करें (यदि विकल्प उपलब्ध नहीं है, तो इसका मतलब है कि आपका डोमेन हमारे BasicDNS/ PremiumDNS / FreeDNS का उपयोग नहीं कर रहा है) : 3) प्रकार के लिए एक रिकॉर्ड का चयन करें और उस होस्ट को दर्ज करें जिसे आप अपने सर्वर आईपी पते पर इंगित करना चाहते हैं: - @ को आपके रूट डोमेन ( domainname.tld ) को इंगित करने के लिए होस्ट के रूप में उपयोग किया जाना चाहिए - www.domainname.tld उपडोमेन के लिए रिकॉर्ड सेट करने के लिए www का उपयोग किया जाना चाहिए - [customhostname] का उपयोग उपडोमेन सेट अप करने और इसे आपके होस्टिंग सर्वर पर इंगित करने के लिए किया जा सकता है (उदाहरण के लिए, होस्ट ब्लॉग blog.domainname.tld को आपके होस्टिंग पर इंगित करेगा) - * को वाइल्डकार्ड उपडोमेन सेट अप करने के लिए होस्ट के रूप में दर्ज किया जाना चाहिए (जिसका अर्थ है कि यह आपके होस्टिंग पर सभी गैर-मौजूद उपडोमेन को इंगित करेगा)। 4) इसके बाद, वैल्यू फील्ड में अपने होस्टिंग सर्वर का आईपी एड्रेस डालें : 5) आप TTL को ऑटोमैटिक (30 मिनट) के तौर पर छोड़ सकते हैं या ड्रॉप-डाउन मेनू से कोई भी कस्टम वैल्यू चुन सकते हैं: कृपया ध्यान दें : TTL वह समय होता है, जिसमें आपके होस्ट रिकॉर्ड का डेटा रिकॉर्ड अपडेट या हटाए जाने के बाद भी बना रहता है। अगर आप सुनिश्चित नहीं हैं कि किस TTL का इस्तेमाल करना है, तो इसे ऑटोमैटिक के तौर पर ही रहने दें । 6) सभी जानकारियां डालने के बाद, उन्हें हरे रंग के आइकन सेव करें : आमतौर पर, नए बनाए गए रिकॉर्ड्स को प्रभावी होने में लगभग 30 मिनट लगते हैं। कुछ होस्टिंग प्रोवाइडर आपसे अतिरिक्त रिकॉर्ड बनाने के लिए भी कह सकते हैं (जैसे URL रीडायरेक्ट या CNAME)। ये रिकॉर्ड A रिकॉर्ड्स की तरह ही सेट किए जा सकते हैं। आपको बस संबंधित टाइप चुनना होगा।
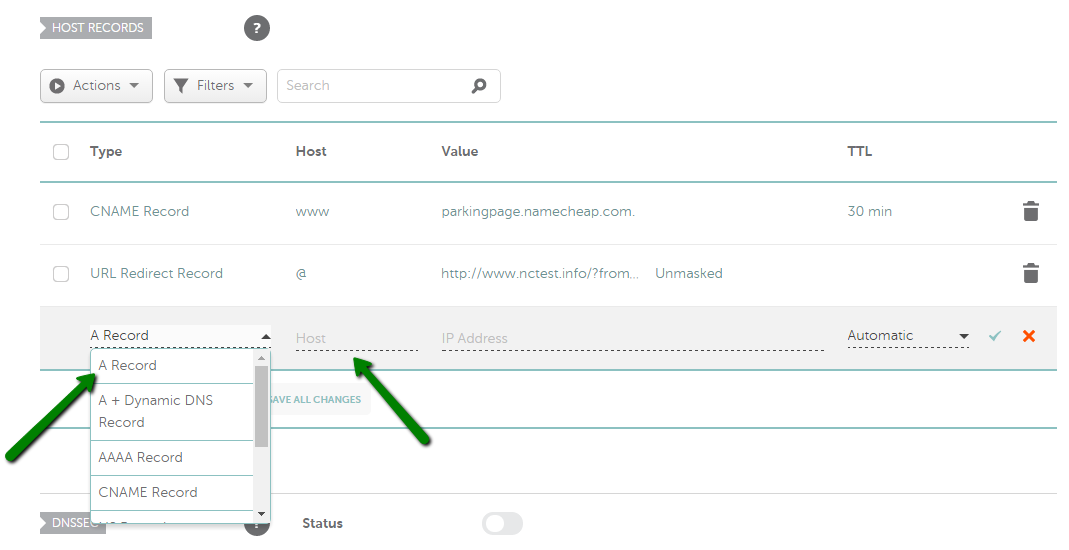
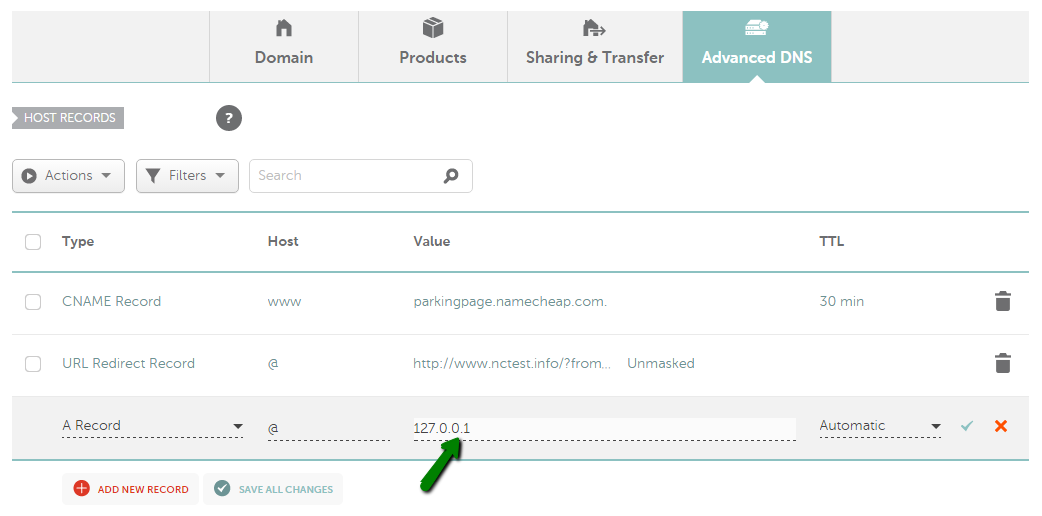
ड्रॉप-डाउन मेनू से रिकॉर्ड चुनें और अपने होस्टिंग प्रदाता से प्राप्त मूल्य
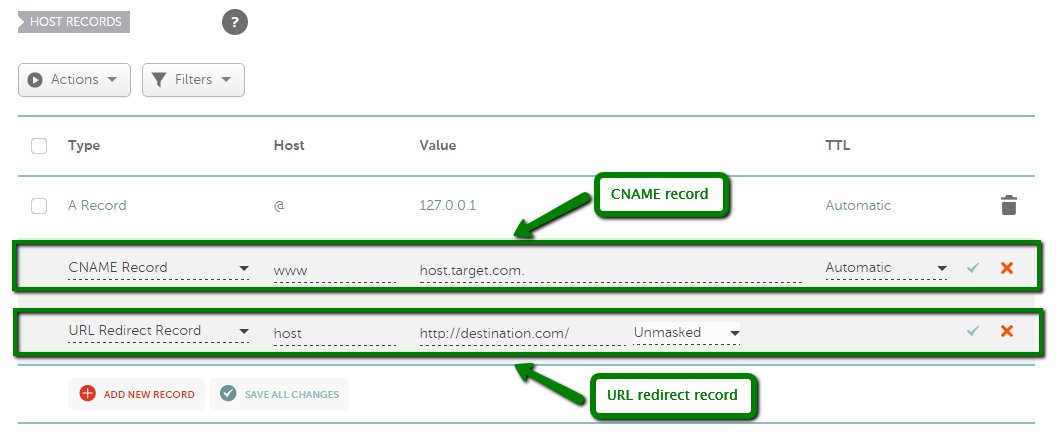
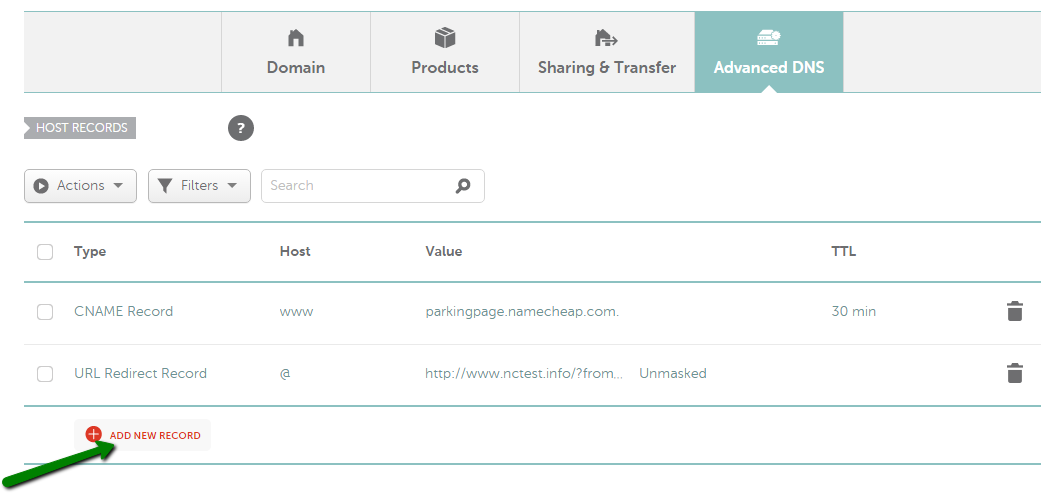
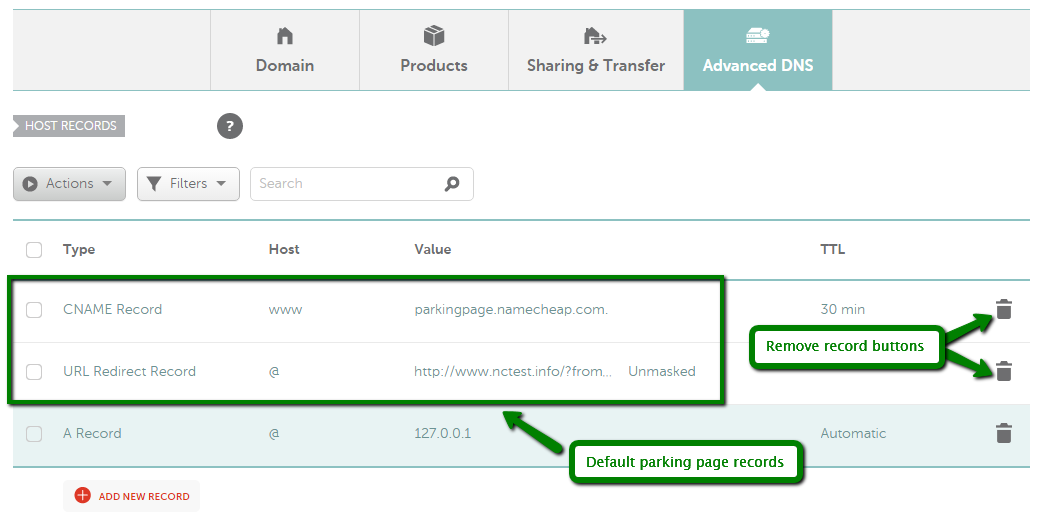
दर्ज करें: रिकॉर्ड्स जोड़े जाने के बाद, आपको यह जांचना होगा कि क्या समान होस्ट नाम के लिए कोई रिकॉर्ड हैं और उन्हें हटा दें क्योंकि वे आपके रिकॉर्ड्स के साथ संघर्ष करेंगे। आपको जिन रिकॉर्ड्स की जांच करने की आवश्यकता है वे अनमास्क्ड/मास्क्ड/स्थायी रीडायरेक्ट, ए या CNAME रिकॉर्ड प्रकार के हो सकते हैं। एक नए पंजीकृत डोमेन में हमारे पार्किंग पेज
के रिकॉर्ड डिफ़ॉल्ट रूप से सेट होंगे। ये रिकॉर्ड @ होस्ट के लिए URL रीडायरेक्ट हैं जो http://www.domainname.tld/ की ओर इशारा करते हैं और www होस्ट के लिए CNAME रिकॉर्ड जो parkingpage.namecheap.com की ओर इशारा करते हैं । इन रिकॉर्ड्स को हमेशा अपने डोमेन के लिए कस्टम होस्ट रिकॉर्ड सेट करने के बाद हटा दिया जाना चाहिए। विरोधाभासी रिकॉर्ड्स को हटाने के लिए, संबंधित रिकॉर्ड के बगल में काले ट्रैश बिन आइकन को दबाएं
यदि आपके कोई प्रश्न हों तो कृपया हमारी सहायता टीम से संपर्क करें ।
thanks for visite to this Website guys✌👇👇😉👐 ....................
👇👇🙏🙏 please support to my social media accounts